top of page
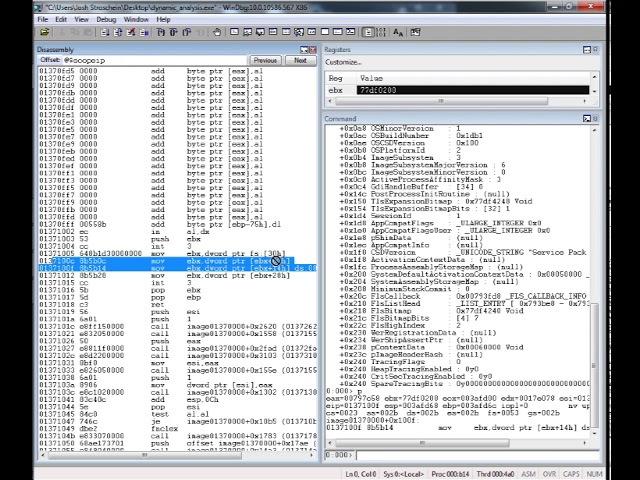

Locating DLL Name from the Process Environment Block (PEB)
I often encounter software, especially when performing malware analysis, that dynamically constructs it’s own import table. This can be...

Josh Stroschein
Feb 10, 20245 min read


Emotet Maldoc Analysis – Embedded DLL and CertUtil for Base64 Decoding
On 11/10/2020, AnyRun posted an Emotet maldoc that utilized CertUtil to decode a DLL payload that was used for unpacking and running the...

Josh Stroschein
Dec 2, 20201 min read


Maldoc drops DLL and executes via ExecuteExcel4Macro
Behavioral information is a key indicator used to determine if an office document is malicious or not. I’ve recently seen a series of...

Josh Stroschein
Mar 25, 20203 min read


Debugging a 32 or 64-bit DLL with WinDbg
Debugging a DLL is not quite as straight forward as an executable, since you have to use rundll32 to load it and invoke DllMain. This is...

Josh Stroschein
Mar 16, 20182 min read
bottom of page





