top of page
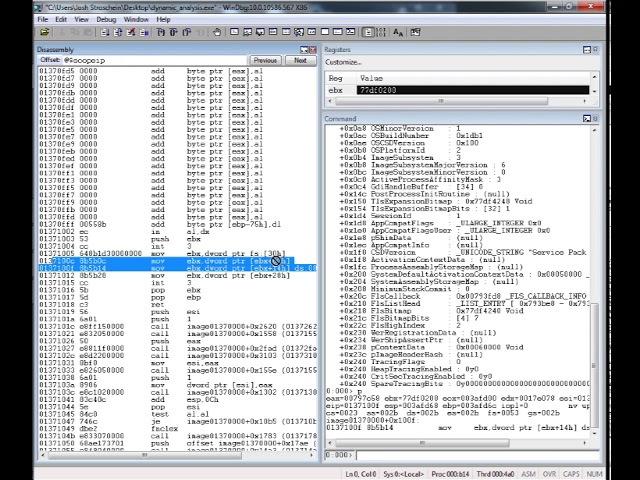

Locating DLL Name from the Process Environment Block (PEB)
I often encounter software, especially when performing malware analysis, that dynamically constructs it’s own import table. This can be...
Josh Stroschein
Feb 10, 20245 min read
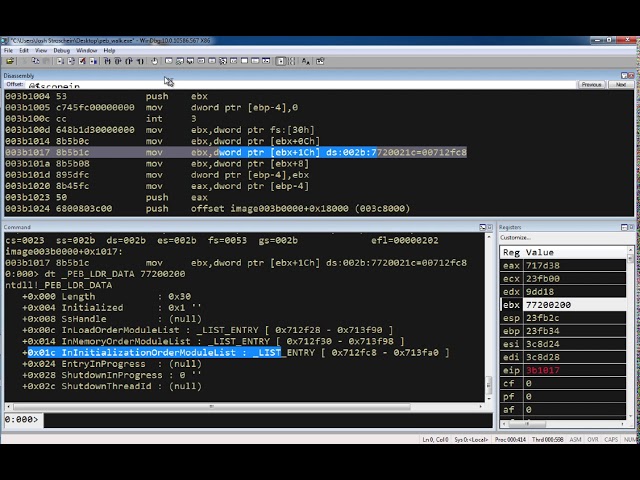

Exploring the Process Environment Block (PEB) with WinDbg
The source code for this example can be found here. The assembly is: mov ebx, fs:[ 0x30 ] ; // get a pointer to the PEB mov ebx, [ ebx +...
Josh Stroschein
Feb 10, 20241 min read


Creating an IDA Python Plugin for Static XOR String Deobfuscation
In this video, we’ll explore a recent XLS document that drops and executes a DLL using RUNDLL32. The DLL is small and only used to...
Josh Stroschein
Jan 6, 20211 min read


Debugging a 32 or 64-bit DLL with WinDbg
Debugging a DLL is not quite as straight forward as an executable, since you have to use rundll32 to load it and invoke DllMain. This is...
Josh Stroschein
Mar 16, 20182 min read
bottom of page





